Mon, September 4, 2006, 05:20 PM under
Windows |
Vista |
UAC
In the office today I was reading a popular PC magasine here in the UK and in the contents it said Dave (sorry I forget surname) looks at User Account Control in Windows Vista. I went to the page and read the article that left me quite disappointed. First, it doesn't really explain the goals behind UAC and how UAC achieves that: this information is available online (two clicks from my blog entry on
User Account Control). Second, over half of the article is basically what seems to me a rant on the 'virtualization' feature (again, I cover virtualization on my
UAC post). While I advise devs not to take advantage of virtualisation, I understand its purpose in offering crutches to some legacy applications that would otherwise break. In any case, the most disappointing thing about the article was that it didn't even mention how to turn off virtualization. While I did this at the nugget I link to from
here, let's repeat it in written form.
1. In your Windows start menu go to the search box and type "sec" to bring up the "Local Security Policy"
2. Navigate to 'Security Settings->Local Policies->Security Options' and scroll to the bottom.
3. There you'll find 9 policies pertaining to User Account Control. Double click on the last one ("Virtualize file and registry write failures to per-user locations")
4. Change the value from Enabled to Disabled
With Vista RC1 there is an improvement to the dialogs that come up for each policy. There is an additional tab: "Explain". Click on this one to read about what the policy does :-) For the policy we've been talking about it looks like this:
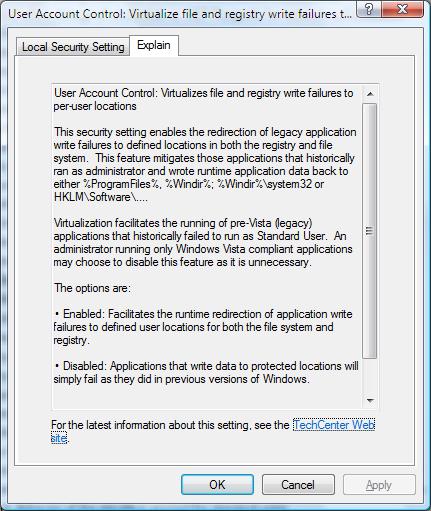
I leave it to you to read the explanations for the other 8 policies:
- Switch to the secure desktop when prompting for elevation
- Run all users, including administrators, as standard users
- Only elevate UIAccess applications that are installed in secure locations
- Only elevate executables that are signed and validated
- Detect application installations and prompt for elevation
- Behavior of the elevation prompt for standard users
- Behavior of the elevation prompt for administrators in Admin Approval Mode
- Admin Approval Mode for the Built-in Administrator account
BTW, with RC1 (build 5600), the number of UAC prompts you get is significantly smaller than earlier builds so go check it out!